-
Type:
Bug
-
Resolution: Fixed
-
Priority:
Major - P3
-
Affects Version/s: 8.0.0-rc0
-
Component/s: Internal Code
-
Server Security
-
Fully Compatible
-
ALL
-
v8.0, v7.0
-
Security 2024-04-29
-
None
-
3
-
None
-
None
-
None
-
None
-
None
-
None
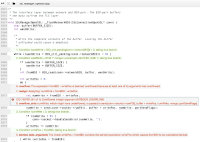
Overflowed integer argument
The argument will be too small or even negative, likely resulting in unexpected behavior (for example, under-allocation in a memory allocation function). An integer overflow occurs, with the overflowed value used as an argument to a function
/src/mongo/util/net/ssl_manager_openssl.cpp:3079: INTEGER_OVERFLOW 139793 The check "writePos < fromBIO" contains the tainted expression "writePos" which causes "fromBIO" to be considered tainted.
/src/mongo/util/net/ssl_manager_openssl.cpp:3073: INTEGER_OVERFLOW 139793 The expression "fromBIO - writePos" is deemed overflowed because at least one of its arguments has overflowed.
/src/mongo/util/net/ssl_manager_openssl.cpp:3073: INTEGER_OVERFLOW 139793 Assigning: "numWrite" = "fromBIO - writePos".
/src/mongo/util/net/ssl_manager_openssl.cpp:3074: INTEGER_OVERFLOW 139793 "numWrite", which might have underflowed, is passed to "send(conn->socket->rawFD(), buffer + writePos, numWrite, mongo::portSendFlags)".